AirTag Lost Mode Vulnerability Can Redirect to Malicious Sites
よく読まれている記事
1Apple announces "fourth product" on March 8, Bloomberg's famous reporter predicts
2Right before the announcement of SE3! iPhone 12 sale held-9,800 yen at MNP
3[Final update] SE 3, M1 iPad Air, Mac Studio related products announced!
4Research results on accuracy of smartwatch with non-puncture blood glucose measurement function published in Nature
5Google Pixel 6a Benchmark Score Reported-Equipped Chip, RAM Capacity?
特集
新着記事
[Final update] SE 3, M1 iPad Air, Mac Studio related products announced!
iPhone SE (3rd generation) will not be reduced in price-MagSafe compatible and extended drive time?
Rumored that iPad Air (5th generation) M1, 128GB, Wi-Fi is 62,800 yen including tax
Apple online store enters the annual maintenance before the event. Are you sure about the new product launch?
Apple readying 5K and 7K displays? Garman's prediction
83.9% of Garake users in their 60s and 70s are aware of the end of 3G, smartphone usage rate is 90%
オフィシャルサイト
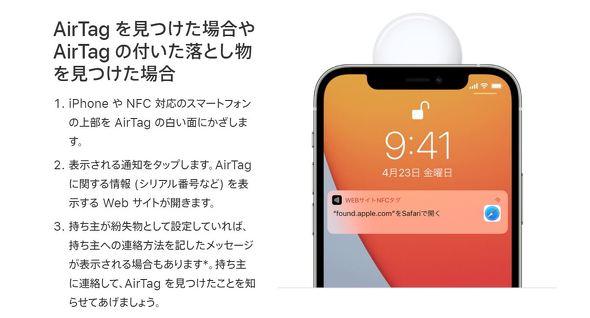
twitter@iPhoneMania_jp からのツイート2021年9月29日09時43分読了まで 約 2分29秒他の人のAirTagを見つけた場合、iPhoneなどにAirTagをかざすと持ち主への連絡方法を確認できる機能が、フィッシング詐欺に悪用される可能性があることが、米セキュリティ情報サイトの「Krebs on Security」の報告で明らかとなりました。Possible redirects to malicious sites
Setting the AirTag to Lost Mode generates a URL of "https://found.apple.com" that allows the AirTag owner to register a contact phone number or email address. When the person who finds the AirTag holds the top of their iPhone or NFC-enabled smartphone over the white surface of the AirTag, they are automatically guided to the URL containing the owner's contact information. You do not need to log in or enter any personal information to view the owner's contact information. According to Krebs on Security, Lost Mode doesn't prevent users from inserting arbitrary computer codes into the phone number field, so anyone who scans an AirTag could land on a fake iCloud login page or malicious website. You may be redirected. People who do not know that their personal information is unnecessary to view the AirTag owner's information may be tricked into providing their iCloud login information or other personal information, or be redirected maliciously. You may end up downloading software from a site with
Security Consultant Bobby Raunch Discovers Vulnerability
The AirTag flaw was discovered by security consultant Bobby Larch, who told Krebs on Security that the vulnerability makes AirTag dangerous. "I don't know of any other example where such a low-cost consumer tracker could be weaponized," he said. Larch reported the vulnerability to Apple on June 20, and the company spent months investigating. The company told Lurch last week that an upcoming update would address the vulnerability and asked him not to speak publicly. Lurch said Apple didn't respond to questions about whether the bug he reported would qualify for its "Security Bounty Program," which provides bounties for discovering vulnerabilities. I am told it has been published. Last week, security researcher Dennis Tokarev, aka illusionofchaos, disclosed multiple iOS zero-day vulnerabilities. Apple ignored his report and did not fix the vulnerability for months. Apple has apologized for the incident, but has continued to be criticized for its security bounty program and its slow response to reports. Source: Krebs on Security via MacRumors (m7000)
--PR--[Official] - Securely buy and reserve your iPhone online!
→ SoftBank Online Shop
→ au online shop
→ docomo online shop
→ Rakuten Mobile Online Shop
カテゴリ : AirTag, 最新情報タグ :AirTag, Apple, iPhone, バグ, 脆弱性▼ 最新情報を受け取る